Business Email Compromise attacks increased to 10.6% of email-based social engineering over the last 12 Months; Conversation hijacking up 70%, Barracuda Reports
New Barracuda report shows how targeted email threats are evolving in the age of AI
- Barracuda’s Email Threats and Trends report, volume 1, shows that more advanced and targeted email-based threats are increasing year on year.
- Business email compromise now accounts for 10.6% of social engineering attacks.
- Conversation hijacking has risen by 70% since 2022.
- Attackers are leveraging QR codes, popular webmail services, and URL shorteners.
Barracuda Networks, Inc., a trusted partner and leading provider of cloud-first security solutions, published Email Threats and Trends, Vol. 1, which shows that over the last 12 months business email compromise attacks have increased to account for 10.6% of email-based social engineering. Conversation hijacking has risen by 70% since 2022, despite being a resource-intensive approach for attackers.
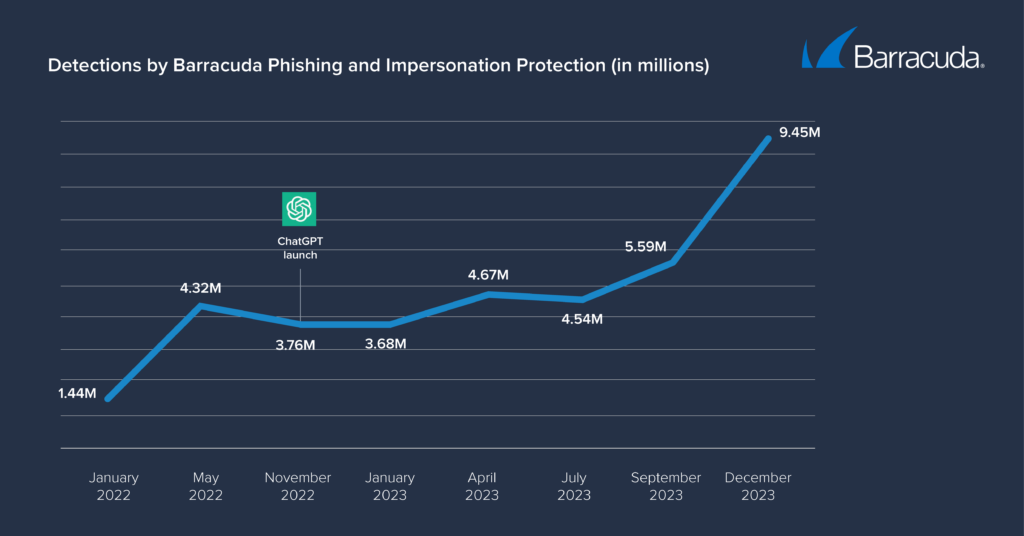
Barracuda researchers analyzed 69 million attacks across 4.5 million mailboxes over a year. The results reveal how cybercriminals are adapting their tactics and taking advantage of the ways generative AI can help them scale their attacks, bypass traditional security measures, and target and trick potential victims.
The findings show that:
- Business email compromise (BEC) attacks made up more than 1 in 10 of all social engineering attacks in 2023, and the numbers show a steady increase over time. BEC attacks accounted for 8% in 2022 and 9% in 2021.
- Conversation hijacking made up 0.5% of the social engineering attacks in the past year, an increase of almost 70% compared to 0.3% in 2022. Conversation hijacking attacks require a lot of effort to execute, but the payouts can be significant.
- Around 1 in 20 mailboxes were targeted with QR code attacks in the last quarter of 2023. QR code attacks are difficult to detect using traditional email filtering methods. They also take victims away from corporate machines and force them to use a personal device, such as a phone or iPad, which isn’t protected by corporate security software.
- Gmail was the most popular free webmail service used for social engineering. In 2023, Gmail accounted for 22% of the domains used for social engineering attacks, according to Barracuda’s data. Just over half the detected Gmail attacks were used for BEC attacks.
- bit.ly was used in nearly 40% of social engineering attacks that include a shortened URL. URL shorteners condense the link, so the actual link of the site becomes obscured with random letters or numbers. Using this tactic can disguise the true nature and destination of the link.
“IT and security professionals need to stay focused on the evolution of email threats and what this means for security measures and incident response,” said Sheila Hara, Sr. Director of Product Management at Barracuda. “This involves understanding how attackers can leverage generative AI to advance and scale their activities, and the latest tactics they’re using to make it past security controls. The best defense is AI-powered cloud email security technology that can adapt quickly to a changing landscape and doesn’t solely rely on looking for malicious links or attachments.”







